While I like Taylor Swift, I prefer Olivia Rodrigo. It was really the spectacular “Vampire” that tipped the balance for me, and since then I really liked “Drivers license” and “Traitor”. I love the balance she strikes between really softly spoken sections and full-on passionate belting. Now, I realise that as a 50-something bloke I’m not exactly her target demographic, but frankly, I don’t care, she’s great! I’m also a big fan of Aaron Francis‘ positive outlook, especially his “you can just do stuff” viewpoint. Long story short, I thought I’d try writing an Olivia Rodrigo-style song, and here it is, “Something Good”.
Like the best of such songs, it’s a breakup song, with a strong contrast between quiet, introverted self-blame, and a massive, triumphant sense of escape . As can be ascertained from most of my other songs, there’s no chance I’m going to sing like a teenage girl, so I thought I’d give my usual synthetic vocalist a workout. I also discovered a feature of this software that I’d somehow missed before – it’s possible to automate voice parameters over time. I’d previously done such changes by using multiple vocal tracks with different parameters, but that’s a bit clunky; now I can do smooth changes, and it’s totally cool. It’s how I do the rising passion before the first chorus and the quiet back-off at the end of each chorus; all one track with automation.
Putting myself in the shoes of this notional teenager that’s dropping a toxic ex (I mean, that’s not me, but empathy, right?), I nurtured a little crop of somewhat stereotypical lyrics; it’s a song, not high literature! I’m quite pleased with them overall: decent density, some good rhymes, and no problems with awkward timing or orphaned syllables.
It’s a proper ballad, at a really slow 50bpm, but has a double-tempo 100bpm section, an idea I straightforwardly stole from “Vampire”. I don’t know if it’s just the specific voice I’m using, but the last line of that section (“make up with a kiss”) is pure Katy Perry.
The backing track uses a fairly standard set of instruments. I’m using drum sounds from Klevgrand’s “Slammer” industrial drum kit. The filter-sweepy bass is courtesy of Logic’s Alchemy and lots of automation, the backing pad a simple RetroSyn patch. The piano is Logic’s “vintage upright”. I played the guitar part on my Squier Strat.
The distortion on the vocals in the fast section is by Logic’s ChromaGlow, and the overall reverb is by ChromaVerb.
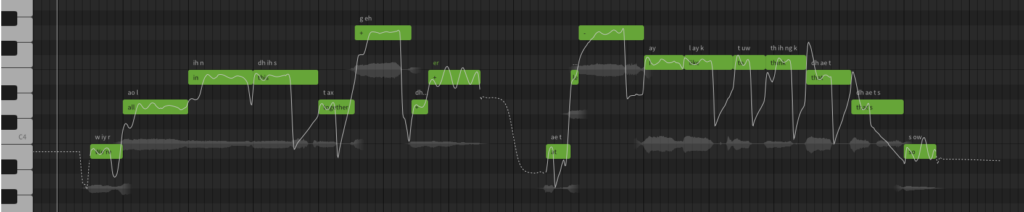
Creating the vocal tracks was quite tricky; there are a lot of lyrics and timing is really tight in places; it’s hard to make things sound natural when dragging blocks around a grid, so I did lots of singing to myself while I was out skiing to practice the timings. I love the “breath” sound that’s available in SV, it’s just so believable!
I wrote the melody first, and then got some chord progression suggestions from Mistral Chat, in particular the use of the occasional A♭sus4 and Esus4 I would not have otherwise thought of, but otherwise there’s nothing complicated in here – all basic triads and 5ths.
There are some very strong contrasts in the song, from the harsh synthetic bass sweep in the intro, through the cut-back piano and super-dry vocal bridge (“There’s no space for fantasy…”), clean simplicity in the verses, minimalist distorted guitars and vocals on the second bridge, to the symphonic, operatic chorus. I’m pretty pleased with this one.
[Verse]
I’d like to go one day alone
without you bringing me down.
A single day without having to atone
for all the things that you said.
Something clean, so elegant and simple
that won’t break my heart again.
[Bridge]
There’s no space for fantasy,
no room for promises.
Just go with what seems right;
I’m gonna leave without a fight
[Chorus]
Something good is sure to come to me.
I’m on my way to something so good.
I’ve had enough of picking up the pieces
of the something good that we used to have.
It’s time to stop all this pretending,
to fool myself that it wasn’t so bad.
I’m moving on to something new,
hoping it turns into something good.
[Verse]
You used to say you’d be better off without me;
now you get to find out.
I’m not used to being alone;
it’s harder than I remember.
But then I look back at the things I won’t miss
and look forward to new things to come
and I realise it will work out just fine,
something new that will be all mine.
[Break]
I know every little word I said is gonna come back and bite me, and
you’re gonna pick up on every last thing and use it just to spite me
but there’s no way I can let you keep on treating me like this;
it’s not the kind of thing you can make up with a kiss.
[Chorus]
Something good is sure to come to me.
I’m on my way to something so good.
I’ve had enough of picking up the pieces
of the something good that we used to have.
It’s time to stop all this pretending,
to fool myself that it wasn’t so bad.
I’m moving on to something new,
hoping it turns into something good.
If you like this song, please consider supporting me by buying my album, “Developer Music” on Bandcamp, and sharing links to my song posts on your socials.